When we start a simulated phishing campaign in collaboration with a company or an organisation, we first carry out a meticulous planning process together with the IT department.
We design an email with content that appears realistic and trust-worthy, so it isn’t too easy for the employees to figure out that it’s a fake phishing email – unless of course you know what to look for.
At an agreed time, we press the SEND button – and thus begins the simulated phishing attack, which sends hundreds or thousands of emails away to the employees of the organisation.
In the following hours and days, we document how easy or difficult it will be for skilled cybercriminals to entice those employees to click on dangerous links, open virus-infested files, or even trick them to reveal their workplace username and password.
The result is disturbing. It turns out that, on average, every fourth employee falls into the phishing trap.
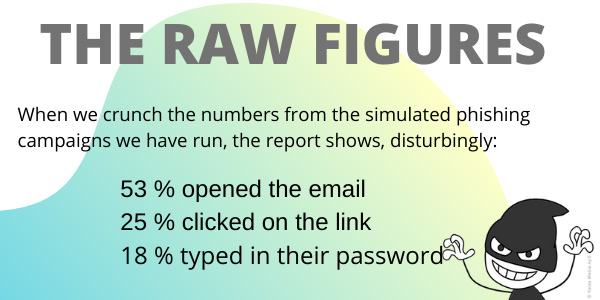
The report’s revelations
Our phishing tool documents that 25% of employees fall into the phishing trap and click on a link they should not have clicked on, while 18% move even further and enter their confidential password on a web page. These are average numbers.
Fortunately, there are also employees who immediately realise that this is a phishing email in circulation. Some of them respond by immediately contacting the IT department to report that something is wrong. Both the IT department and the Service Desk have a busy day as the simulated phishing campaign rolls out.

Hackers love emails
9 out of 10 hacker attacks start with a phishing email. And a study shows that hackers send out over 156 million phishing emails every day.
Another investigation shows that US$18,350 is stolen with phishing emails every single minute.
So let’s face it: hackers are extremely fond of emails – which means that we have to be extremely careful and conscious about what we click on or respond to in our mailboxes.
Source: Computerworld, among others

Three tips for spotting a phishing email
Check the URL: Does it look real? Hover your mouse over the url or clickable word so that you can see which url it is pointing to. Keep an eye out for spelling mistakes, and confirm its validity by looking up the url in another way than by clicking on the link. In a phishing email, there will often be an extra letter in the url, (for instance: wvvw.ikea.com instead of www.ikea.com), or there will be another domain (for example, instead of .dk it says .net).
Check the sender: Look for errors in the email address and if in doubt, you should contact the person listed as the sender to find out if they have sent you an email. And here it is important that you get the person’s correct email address, phone number or contact information from elsewhere.
Check the content: You may be asked to provide personal or sensitive information – do not! Learn more about the the email by copying a unique line from the email, put it in Google Search with quotation marks before and after, and see what others have been writing about this email.

COMPETITION: Win a phishing campaign
Get ready – in the next newsletter we will start a competition where an organisation or company can win a phishing campaign for internal use in the organisation.
Awareness training with just a bit more fun
Humour against hacking is a simple and easy to understand awareness campaign with many e-learning courses, nudging materials, phishing campaigns, LMS, etc.
Everything can be adapted to the individual organisation so you can get started quickly.
Contact
If you would like to have a demonstration of our awareness universe, contact us at info@humouragainsthacking.com.au for an informal chat – and let us show you our material and why it works. 🙂
Contact ‘Humour against hacking’
Copyright © 2020 Kelsa Media & Geelong Media – All rights reserved.
This newsletter was published on 27 October 2020
Sign up for Geelong Media’s newsletter

